Iustin Pop: Somewhat committing to a new sport
 Small lake, but beautiful view
Small lake, but beautiful view
 Small lake, but beautiful view
Small lake, but beautiful view
 As promised, on this post I m going to explain how I ve configured this blog
using
As promised, on this post I m going to explain how I ve configured this blog
using hugo, asciidoctor and the papermod theme, how I publish it using
nginx, how I ve integrated the remark42 comment system and how I ve
automated its publication using gitea and json2file-go.
It is a long post, but I hope that at least parts of it can be interesting for
some, feel free to ignore it if that is not your case
config.yml file is the one shown below (probably some of the
settings are not required nor being used right now, but I m including the
current file, so this post will have always the latest version of it):
baseURL: https://blogops.mixinet.net/
title: Mixinet BlogOps
paginate: 5
theme: PaperMod
destination: public/
enableInlineShortcodes: true
enableRobotsTXT: true
buildDrafts: false
buildFuture: false
buildExpired: false
enableEmoji: true
pygmentsUseClasses: true
minify:
disableXML: true
minifyOutput: true
languages:
en:
languageName: "English"
description: "Mixinet BlogOps - https://blogops.mixinet.net/"
author: "Sergio Talens-Oliag"
weight: 1
title: Mixinet BlogOps
homeInfoParams:
Title: "Sergio Talens-Oliag Technical Blog"
Content: >

taxonomies:
category: categories
tag: tags
series: series
menu:
main:
- name: Archive
url: archives
weight: 5
- name: Categories
url: categories/
weight: 10
- name: Tags
url: tags/
weight: 10
- name: Search
url: search/
weight: 15
outputs:
home:
- HTML
- RSS
- JSON
params:
env: production
defaultTheme: light
disableThemeToggle: false
ShowShareButtons: true
ShowReadingTime: true
disableSpecial1stPost: true
disableHLJS: true
displayFullLangName: true
ShowPostNavLinks: true
ShowBreadCrumbs: true
ShowCodeCopyButtons: true
ShowRssButtonInSectionTermList: true
ShowFullTextinRSS: true
ShowToc: true
TocOpen: false
comments: true
remark42SiteID: "blogops"
remark42Url: "/remark42"
profileMode:
enabled: false
title: Sergio Talens-Oliag Technical Blog
imageUrl: "/images/mixinet-blogops.png"
imageTitle: Mixinet BlogOps
buttons:
- name: Archives
url: archives
- name: Categories
url: categories
- name: Tags
url: tags
socialIcons:
- name: CV
url: "https://www.uv.es/~sto/cv/"
- name: Debian
url: "https://people.debian.org/~sto/"
- name: GitHub
url: "https://github.com/sto/"
- name: GitLab
url: "https://gitlab.com/stalens/"
- name: Linkedin
url: "https://www.linkedin.com/in/sergio-talens-oliag/"
- name: RSS
url: "index.xml"
assets:
disableHLJS: true
favicon: "/favicon.ico"
favicon16x16: "/favicon-16x16.png"
favicon32x32: "/favicon-32x32.png"
apple_touch_icon: "/apple-touch-icon.png"
safari_pinned_tab: "/safari-pinned-tab.svg"
fuseOpts:
isCaseSensitive: false
shouldSort: true
location: 0
distance: 1000
threshold: 0.4
minMatchCharLength: 0
keys: ["title", "permalink", "summary", "content"]
markup:
asciidocExt:
attributes:
backend: html5s
extensions: ['asciidoctor-html5s','asciidoctor-diagram']
failureLevel: fatal
noHeaderOrFooter: true
preserveTOC: false
safeMode: unsafe
sectionNumbers: false
trace: false
verbose: false
workingFolderCurrent: true
privacy:
vimeo:
disabled: false
simple: true
twitter:
disabled: false
enableDNT: true
simple: true
instagram:
disabled: false
simple: true
youtube:
disabled: false
privacyEnhanced: true
services:
instagram:
disableInlineCSS: true
twitter:
disableInlineCSS: true
security:
exec:
allow:
- '^asciidoctor$'
- '^dart-sass-embedded$'
- '^go$'
- '^npx$'
- '^postcss$'disableHLJS and assets.disableHLJS are set to true; we plan to use
rouge on adoc and the inclusion of the hljs assets adds styles that
collide with the ones used by rouge.ShowToc is set to true and the TocOpen setting is set to false to
make the ToC appear collapsed initially. My plan was to use the asciidoctor
ToC, but after trying I believe that the theme one looks nice and I don t
need to adjust styles, although it has some issues with the html5s
processor (the admonition titles use <h6> and they are shown on the ToC,
which is weird), to fix it I ve copied the layouts/partial/toc.html to my
site repository and replaced the range of headings to end at 5 instead of
6 (in fact 5 still seems a lot, but as I don t think I ll use that heading
level on the posts it doesn t really matter).params.profileMode values are adjusted, but for now I ve left it disabled
setting params.profileMode.enabled to false and I ve set the
homeInfoParams to show more or less the same content with the latest posts
under it (I ve added some styles to my custom.css style sheet to center the
text and image of the first post to match the look and feel of the profile).asciidocExt section I ve adjusted the backend to use html5s,
I ve added the asciidoctor-html5s and asciidoctor-diagram extensions to
asciidoctor and adjusted the workingFolderCurrent to true to make
asciidoctor-diagram work right (haven t tested it yet).asciidoctor using the html5s processor I ve added some files to
the assets/css/extended directory:
assets/css/extended/custom.css to
make the homeInfoParams look like the profile page and I ve also changed a
little bit some theme styles to make things look better with the html5s
output:/* Fix first entry alignment to make it look like the profile */
.first-entry text-align: center;
.first-entry img display: inline;
/**
* Remove margin for .post-content code and reduce padding to make it look
* better with the asciidoctor html5s output.
**/
.post-content code margin: auto 0; padding: 4px; assets/css/extended/adoc.css with some styles
taken from the asciidoctor-default.css, see this
blog
post about the original file; mine is the same after formatting it with
css-beautify and editing it to use variables for
the colors to support light and dark themes:/* AsciiDoctor*/
table
border-collapse: collapse;
border-spacing: 0
.admonitionblock>table
border-collapse: separate;
border: 0;
background: none;
width: 100%
.admonitionblock>table td.icon
text-align: center;
width: 80px
.admonitionblock>table td.icon img
max-width: none
.admonitionblock>table td.icon .title
font-weight: bold;
font-family: "Open Sans", "DejaVu Sans", sans-serif;
text-transform: uppercase
.admonitionblock>table td.content
padding-left: 1.125em;
padding-right: 1.25em;
border-left: 1px solid #ddddd8;
color: var(--primary)
.admonitionblock>table td.content>:last-child>:last-child
margin-bottom: 0
.admonitionblock td.icon [class^="fa icon-"]
font-size: 2.5em;
text-shadow: 1px 1px 2px var(--secondary);
cursor: default
.admonitionblock td.icon .icon-note::before
content: "\f05a";
color: var(--icon-note-color)
.admonitionblock td.icon .icon-tip::before
content: "\f0eb";
color: var(--icon-tip-color)
.admonitionblock td.icon .icon-warning::before
content: "\f071";
color: var(--icon-warning-color)
.admonitionblock td.icon .icon-caution::before
content: "\f06d";
color: var(--icon-caution-color)
.admonitionblock td.icon .icon-important::before
content: "\f06a";
color: var(--icon-important-color)
.conum[data-value]
display: inline-block;
color: #fff !important;
background-color: rgba(100, 100, 0, .8);
-webkit-border-radius: 100px;
border-radius: 100px;
text-align: center;
font-size: .75em;
width: 1.67em;
height: 1.67em;
line-height: 1.67em;
font-family: "Open Sans", "DejaVu Sans", sans-serif;
font-style: normal;
font-weight: bold
.conum[data-value] *
color: #fff !important
.conum[data-value]+b
display: none
.conum[data-value]::after
content: attr(data-value)
pre .conum[data-value]
position: relative;
top: -.125em
b.conum *
color: inherit !important
.conum:not([data-value]):empty
display: none
theme-vars.css
file that changes the highlighted code background color and adds the color
definitions used by the admonitions::root
/* Solarized base2 */
/* --hljs-bg: rgb(238, 232, 213); */
/* Solarized base3 */
/* --hljs-bg: rgb(253, 246, 227); */
/* Solarized base02 */
--hljs-bg: rgb(7, 54, 66);
/* Solarized base03 */
/* --hljs-bg: rgb(0, 43, 54); */
/* Default asciidoctor theme colors */
--icon-note-color: #19407c;
--icon-tip-color: var(--primary);
--icon-warning-color: #bf6900;
--icon-caution-color: #bf3400;
--icon-important-color: #bf0000
.dark
--hljs-bg: rgb(7, 54, 66);
/* Asciidoctor theme colors with tint for dark background */
--icon-note-color: #3e7bd7;
--icon-tip-color: var(--primary);
--icon-warning-color: #ff8d03;
--icon-caution-color: #ff7847;
--icon-important-color: #ff3030
font-awesome, so I ve downloaded its resources for
version 4.7.0 (the one used by asciidoctor) storing the
font-awesome.css into on the assets/css/extended dir (that way it is
merged with the rest of .css files) and copying the fonts to the
static/assets/fonts/ dir (will be served directly):FA_BASE_URL="https://cdnjs.cloudflare.com/ajax/libs/font-awesome/4.7.0"
curl "$FA_BASE_URL/css/font-awesome.css" \
> assets/css/extended/font-awesome.css
for f in FontAwesome.otf fontawesome-webfont.eot \
fontawesome-webfont.svg fontawesome-webfont.ttf \
fontawesome-webfont.woff fontawesome-webfont.woff2; do
curl "$FA_BASE_URL/fonts/$f" > "static/assets/fonts/$f"
donecss
compatible with rouge) so we need a css to do the highlight styling; as
rouge provides a way to export them, I ve created the
assets/css/extended/rouge.css file with the thankful_eyes theme:rougify style thankful_eyes > assets/css/extended/rouge.csshtml5s backend with admonitions I ve added a
variation of the example found on this
blog
post to assets/js/adoc-admonitions.js:// replace the default admonitions block with a table that uses a format
// similar to the standard asciidoctor ... as we are using fa-icons here there
// is no need to add the icons: font entry on the document.
window.addEventListener('load', function ()
const admonitions = document.getElementsByClassName('admonition-block')
for (let i = admonitions.length - 1; i >= 0; i--)
const elm = admonitions[i]
const type = elm.classList[1]
const title = elm.getElementsByClassName('block-title')[0];
const label = title.getElementsByClassName('title-label')[0]
.innerHTML.slice(0, -1);
elm.removeChild(elm.getElementsByClassName('block-title')[0]);
const text = elm.innerHTML
const parent = elm.parentNode
const tempDiv = document.createElement('div')
tempDiv.innerHTML = <div class="admonitionblock $ type ">
<table>
<tbody>
<tr>
<td class="icon">
<i class="fa icon-$ type " title="$ label "></i>
</td>
<td class="content">
$ text
</td>
</tr>
</tbody>
</table>
</div>
const input = tempDiv.childNodes[0]
parent.replaceChild(input, elm)
)layouts/partials/extend_footer.html file
adding the following lines to it:
- $admonitions := slice (resources.Get "js/adoc-admonitions.js")
resources.Concat "assets/js/adoc-admonitions.js" minify fingerprint
<script defer crossorigin="anonymous" src=" $admonitions.RelPermalink "
integrity=" $admonitions.Data.Integrity "></script>layouts/partials/comments.html with the following content
based on the remark42
documentation, including extra code to sync the dark/light setting with the
one set on the site:
<div id="remark42"></div>
<script>
var remark_config =
host: .Site.Params.remark42Url ,
site_id: .Site.Params.remark42SiteID ,
url: .Permalink ,
locale: .Site.Language.Lang
;
(function(c)
/* Adjust the theme using the local-storage pref-theme if set */
if (localStorage.getItem("pref-theme") === "dark")
remark_config.theme = "dark";
else if (localStorage.getItem("pref-theme") === "light")
remark_config.theme = "light";
/* Add remark42 widget */
for(var i = 0; i < c.length; i++)
var d = document, s = d.createElement('script');
s.src = remark_config.host + '/web/' + c[i] +'.js';
s.defer = true;
(d.head d.body).appendChild(s);
)(remark_config.components ['embed']);
</script>remark42 I ve also added the following inside
the layouts/partials/extend_footer.html file:
- if (not site.Params.disableThemeToggle)
<script>
/* Function to change theme when the toggle button is pressed */
document.getElementById("theme-toggle").addEventListener("click", () =>
if (typeof window.REMARK42 != "undefined")
if (document.body.className.includes('dark'))
window.REMARK42.changeTheme('light');
else
window.REMARK42.changeTheme('dark');
);
</script>
- end theme-toggle button is pressed we change the remark42
theme before the PaperMod one (that s needed here only, on page loads the
remark42 theme is synced with the main one using the code from the
layouts/partials/comments.html shown earlier).docker-compose with the following
configuration:
version: "2"
services:
hugo:
build:
context: ./docker/hugo-adoc
dockerfile: ./Dockerfile
image: sto/hugo-adoc
container_name: hugo-adoc-blogops
restart: always
volumes:
- .:/documents
command: server --bind 0.0.0.0 -D -F
user: $ APP_UID :$ APP_GID
nginx:
image: nginx:latest
container_name: nginx-blogops
restart: always
volumes:
- ./nginx/default.conf:/etc/nginx/conf.d/default.conf
ports:
- 1313:1313
remark42:
build:
context: ./docker/remark42
dockerfile: ./Dockerfile
image: sto/remark42
container_name: remark42-blogops
restart: always
env_file:
- ./.env
- ./remark42/env.dev
volumes:
- ./remark42/var.dev:/srv/var.env file with the current user ID
and GID on the variables APP_UID and APP_GID (if we don t do it the files
can end up being owned by a user that is not the same as the one running the
services):
$ echo "APP_UID=$(id -u)\nAPP_GID=$(id -g)" > .envDockerfile used to generate the sto/hugo-adoc is:
FROM asciidoctor/docker-asciidoctor:latest
RUN gem install --no-document asciidoctor-html5s &&\
apk update && apk add --no-cache curl libc6-compat &&\
repo_path="gohugoio/hugo" &&\
api_url="https://api.github.com/repos/$repo_path/releases/latest" &&\
download_url="$(\
curl -sL "$api_url" \
sed -n "s/^.*download_url\": \"\\(.*.extended.*Linux-64bit.tar.gz\)\"/\1/p"\
)" &&\
curl -sL "$download_url" -o /tmp/hugo.tgz &&\
tar xf /tmp/hugo.tgz hugo &&\
install hugo /usr/bin/ &&\
rm -f hugo /tmp/hugo.tgz &&\
/usr/bin/hugo version &&\
apk del curl && rm -rf /var/cache/apk/*
# Expose port for live server
EXPOSE 1313
ENTRYPOINT ["/usr/bin/hugo"]
CMD [""]asciidoctor
and to use hugo I only need to download the binary from their latest release
at github (as we are using an
image based on alpine we also need to install the
libc6-compat package, but once that is done things are working fine for me so
far).
The image does not launch the server by default because I don t want it to; in
fact I use the same docker-compose.yml file to publish the site in production
simply calling the container without the arguments passed on the
docker-compose.yml file (see later).
When running the containers with docker-compose up (or docker compose up if
you have the docker-compose-plugin package installed) we also launch a nginx
container and the remark42 service so we can test everything together.
The Dockerfile for the remark42 image is the original one with an updated
version of the init.sh script:
FROM umputun/remark42:latest
COPY init.sh /init.shinit.sh is similar to the original, but allows us to use an
APP_GID variable and updates the /etc/group file of the container so the
files get the right user and group (with the original script the group is
always 1001):
#!/sbin/dinit /bin/sh
uid="$(id -u)"
if [ "$ uid " -eq "0" ]; then
echo "init container"
# set container's time zone
cp "/usr/share/zoneinfo/$ TIME_ZONE " /etc/localtime
echo "$ TIME_ZONE " >/etc/timezone
echo "set timezone $ TIME_ZONE ($(date))"
# set UID & GID for the app
if [ "$ APP_UID " ] [ "$ APP_GID " ]; then
[ "$ APP_UID " ] APP_UID="1001"
[ "$ APP_GID " ] APP_GID="$ APP_UID "
echo "set custom APP_UID=$ APP_UID & APP_GID=$ APP_GID "
sed -i "s/^app:x:1001:1001:/app:x:$ APP_UID :$ APP_GID :/" /etc/passwd
sed -i "s/^app:x:1001:/app:x:$ APP_GID :/" /etc/group
else
echo "custom APP_UID and/or APP_GID not defined, using 1001:1001"
fi
chown -R app:app /srv /home/app
fi
echo "prepare environment"
# replace % REMARK_URL % by content of REMARK_URL variable
find /srv -regex '.*\.\(html\ js\ mjs\)$' -print \
-exec sed -i "s % REMARK_URL % $ REMARK_URL g" \;
if [ -n "$ SITE_ID " ]; then
#replace "site_id: 'remark'" by SITE_ID
sed -i "s 'remark' '$ SITE_ID ' g" /srv/web/*.html
fi
echo "execute \"$*\""
if [ "$ uid " -eq "0" ]; then
exec su-exec app "$@"
else
exec "$@"
firemark42 for development is quite minimal:
TIME_ZONE=Europe/Madrid
REMARK_URL=http://localhost:1313/remark42
SITE=blogops
SECRET=123456
ADMIN_SHARED_ID=sto
AUTH_ANON=true
EMOJI=truenginx/default.conf file used to publish the service locally is simple
too:
server
listen 1313;
server_name localhost;
location /
proxy_pass http://hugo:1313;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
location /remark42/
rewrite /remark42/(.*) /$1 break;
proxy_pass http://remark42:8080/;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
main Debian repository:
git to clone & pull the repository,jq to parse json files from shell scripts,json2file-go to save the webhook messages to files,inotify-tools to detect when new files are stored by json2file-go and
launch scripts to process them,nginx to publish the site using HTTPS and work as proxy for
json2file-go and remark42 (I run it using a container),task-spool to queue the scripts that update the deployment.docker and docker compose from the debian packages on the
docker repository:
docker-ce to run the containers,docker-compose-plugin to run docker compose (it is a plugin, so no - in
the name).git repository I ve created a deploy key, added it to gitea
and cloned the project on the /srv/blogops PATH (that route is owned by a
regular user that has permissions to run docker, as I said before).hugoTo compile the site we are using the docker-compose.yml file seen before, to
be able to run it first we build the container images and once we have them we
launch hugo using docker compose run:
$ cd /srv/blogops
$ git pull
$ docker compose build
$ if [ -d "./public" ]; then rm -rf ./public; fi
$ docker compose run hugo --/srv/blogops/public (we remove the
directory first because hugo does not clean the destination folder as
jekyll does).
The deploy script re-generates the site as described and moves the public
directory to its final place for publishing.remark42 with dockerOn the /srv/blogops/remark42 folder I have the following docker-compose.yml:
version: "2"
services:
remark42:
build:
context: ../docker/remark42
dockerfile: ./Dockerfile
image: sto/remark42
env_file:
- ../.env
- ./env.prod
container_name: remark42
restart: always
volumes:
- ./var.prod:/srv/var
ports:
- 127.0.0.1:8042:8080../.env file is loaded to get the APP_UID and APP_GID variables that
are used by my version of the init.sh script to adjust file permissions and
the env.prod file contains the rest of the settings for remark42, including
the social network tokens (see the
remark42 documentation for
the available parameters, I don t include my configuration here because some of
them are secrets).nginx configuration for the blogops.mixinet.net site is as simple as:
server
listen 443 ssl http2;
server_name blogops.mixinet.net;
ssl_certificate /etc/letsencrypt/live/blogops.mixinet.net/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/blogops.mixinet.net/privkey.pem;
include /etc/letsencrypt/options-ssl-nginx.conf;
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem;
access_log /var/log/nginx/blogops.mixinet.net-443.access.log;
error_log /var/log/nginx/blogops.mixinet.net-443.error.log;
root /srv/blogops/nginx/public_html;
location /
try_files $uri $uri/ =404;
include /srv/blogops/nginx/remark42.conf;
server
listen 80 ;
listen [::]:80 ;
server_name blogops.mixinet.net;
access_log /var/log/nginx/blogops.mixinet.net-80.access.log;
error_log /var/log/nginx/blogops.mixinet.net-80.error.log;
if ($host = blogops.mixinet.net)
return 301 https://$host$request_uri;
return 404;
/srv/blogops/nginx/public_html and not on /srv/blogops/public; the reason
for that is that I want to be able to compile without affecting the running
site, the deployment script generates the site on /srv/blogops/public and if
all works well we rename folders to do the switch, making the change feel almost
atomic.gitea at my home and the VM where the blog is served, I m
going to configure the json2file-go to listen for connections on a high port
using a self signed certificate and listening on IP addresses only reachable
through the VPN.
To do it we create a systemd socket to run json2file-go and adjust its
configuration to listen on a private IP (we use the FreeBind option on its
definition to be able to launch the service even when the IP is not available,
that is, when the VPN is down).
The following script can be used to set up the json2file-go configuration:
#!/bin/sh
set -e
# ---------
# VARIABLES
# ---------
BASE_DIR="/srv/blogops/webhook"
J2F_DIR="$BASE_DIR/json2file"
TLS_DIR="$BASE_DIR/tls"
J2F_SERVICE_NAME="json2file-go"
J2F_SERVICE_DIR="/etc/systemd/system/json2file-go.service.d"
J2F_SERVICE_OVERRIDE="$J2F_SERVICE_DIR/override.conf"
J2F_SOCKET_DIR="/etc/systemd/system/json2file-go.socket.d"
J2F_SOCKET_OVERRIDE="$J2F_SOCKET_DIR/override.conf"
J2F_BASEDIR_FILE="/etc/json2file-go/basedir"
J2F_DIRLIST_FILE="/etc/json2file-go/dirlist"
J2F_CRT_FILE="/etc/json2file-go/certfile"
J2F_KEY_FILE="/etc/json2file-go/keyfile"
J2F_CRT_PATH="$TLS_DIR/crt.pem"
J2F_KEY_PATH="$TLS_DIR/key.pem"
# ----
# MAIN
# ----
# Install packages used with json2file for the blogops site
sudo apt update
sudo apt install -y json2file-go uuid
if [ -z "$(type mkcert)" ]; then
sudo apt install -y mkcert
fi
sudo apt clean
# Configuration file values
J2F_USER="$(id -u)"
J2F_GROUP="$(id -g)"
J2F_DIRLIST="blogops:$(uuid)"
J2F_LISTEN_STREAM="172.31.31.1:4443"
# Configure json2file
[ -d "$J2F_DIR" ] mkdir "$J2F_DIR"
sudo sh -c "echo '$J2F_DIR' >'$J2F_BASEDIR_FILE'"
[ -d "$TLS_DIR" ] mkdir "$TLS_DIR"
if [ ! -f "$J2F_CRT_PATH" ] [ ! -f "$J2F_KEY_PATH" ]; then
mkcert -cert-file "$J2F_CRT_PATH" -key-file "$J2F_KEY_PATH" "$(hostname -f)"
fi
sudo sh -c "echo '$J2F_CRT_PATH' >'$J2F_CRT_FILE'"
sudo sh -c "echo '$J2F_KEY_PATH' >'$J2F_KEY_FILE'"
sudo sh -c "cat >'$J2F_DIRLIST_FILE'" <<EOF
$(echo "$J2F_DIRLIST" tr ';' '\n')
EOF
# Service override
[ -d "$J2F_SERVICE_DIR" ] sudo mkdir "$J2F_SERVICE_DIR"
sudo sh -c "cat >'$J2F_SERVICE_OVERRIDE'" <<EOF
[Service]
User=$J2F_USER
Group=$J2F_GROUP
EOF
# Socket override
[ -d "$J2F_SOCKET_DIR" ] sudo mkdir "$J2F_SOCKET_DIR"
sudo sh -c "cat >'$J2F_SOCKET_OVERRIDE'" <<EOF
[Socket]
# Set FreeBind to listen on missing addresses (the VPN can be down sometimes)
FreeBind=true
# Set ListenStream to nothing to clear its value and add the new value later
ListenStream=
ListenStream=$J2F_LISTEN_STREAM
EOF
# Restart and enable service
sudo systemctl daemon-reload
sudo systemctl stop "$J2F_SERVICE_NAME"
sudo systemctl start "$J2F_SERVICE_NAME"
sudo systemctl enable "$J2F_SERVICE_NAME"
# ----
# vim: ts=2:sw=2:et:ai:sts=2mkcert to create the temporary certificates, to install the
package on bullseye the backports repository must be available.json2file-go server we go to the project and enter into
the hooks/gitea/new page, once there we create a new webhook of type gitea
and set the target URL to https://172.31.31.1:4443/blogops and on the secret
field we put the token generated with uuid by the setup script:
sed -n -e 's/blogops://p' /etc/json2file-go/dirlist*webhook section of the app.ini of our gitea
server allows us to call the IP and skips the TLS verification (you can see the
available options on the
gitea
documentation).
The [webhook] section of my server looks like this:
[webhook]
ALLOWED_HOST_LIST=private
SKIP_TLS_VERIFY=truewebhook configured we can try it and if it works our
json2file server will store the file on the
/srv/blogops/webhook/json2file/blogops/ folder.gitea and store the messages on files, but we have to do something to
process those files once they are saved in our machine.
An option could be to use a cronjob to look for new files, but we can do
better on Linux using inotify we will use the inotifywait command from
inotify-tools to watch the json2file output directory and execute a script
each time a new file is moved inside it or closed after writing
(IN_CLOSE_WRITE and IN_MOVED_TO events).
To avoid concurrency problems we are going to use task-spooler to launch the
scripts that process the webhooks using a queue of length 1, so they are
executed one by one in a FIFO queue.
The spooler script is this:
#!/bin/sh
set -e
# ---------
# VARIABLES
# ---------
BASE_DIR="/srv/blogops/webhook"
BIN_DIR="$BASE_DIR/bin"
TSP_DIR="$BASE_DIR/tsp"
WEBHOOK_COMMAND="$BIN_DIR/blogops-webhook.sh"
# ---------
# FUNCTIONS
# ---------
queue_job()
echo "Queuing job to process file '$1'"
TMPDIR="$TSP_DIR" TS_SLOTS="1" TS_MAXFINISHED="10" \
tsp -n "$WEBHOOK_COMMAND" "$1"
# ----
# MAIN
# ----
INPUT_DIR="$1"
if [ ! -d "$INPUT_DIR" ]; then
echo "Input directory '$INPUT_DIR' does not exist, aborting!"
exit 1
fi
[ -d "$TSP_DIR" ] mkdir "$TSP_DIR"
echo "Processing existing files under '$INPUT_DIR'"
find "$INPUT_DIR" -type f sort while read -r _filename; do
queue_job "$_filename"
done
# Use inotifywatch to process new files
echo "Watching for new files under '$INPUT_DIR'"
inotifywait -q -m -e close_write,moved_to --format "%w%f" -r "$INPUT_DIR"
while read -r _filename; do
queue_job "$_filename"
done
# ----
# vim: ts=2:sw=2:et:ai:sts=2systemd service using the following
script:
#!/bin/sh
set -e
# ---------
# VARIABLES
# ---------
BASE_DIR="/srv/blogops/webhook"
BIN_DIR="$BASE_DIR/bin"
J2F_DIR="$BASE_DIR/json2file"
SPOOLER_COMMAND="$BIN_DIR/blogops-spooler.sh '$J2F_DIR'"
SPOOLER_SERVICE_NAME="blogops-j2f-spooler"
SPOOLER_SERVICE_FILE="/etc/systemd/system/$SPOOLER_SERVICE_NAME.service"
# Configuration file values
J2F_USER="$(id -u)"
J2F_GROUP="$(id -g)"
# ----
# MAIN
# ----
# Install packages used with the webhook processor
sudo apt update
sudo apt install -y inotify-tools jq task-spooler
sudo apt clean
# Configure process service
sudo sh -c "cat > $SPOOLER_SERVICE_FILE" <<EOF
[Install]
WantedBy=multi-user.target
[Unit]
Description=json2file processor for $J2F_USER
After=docker.service
[Service]
Type=simple
User=$J2F_USER
Group=$J2F_GROUP
ExecStart=$SPOOLER_COMMAND
EOF
# Restart and enable service
sudo systemctl daemon-reload
sudo systemctl stop "$SPOOLER_SERVICE_NAME" true
sudo systemctl start "$SPOOLER_SERVICE_NAME"
sudo systemctl enable "$SPOOLER_SERVICE_NAME"
# ----
# vim: ts=2:sw=2:et:ai:sts=2hugo with docker
compose,#!/bin/sh
set -e
# ---------
# VARIABLES
# ---------
# Values
REPO_REF="refs/heads/main"
REPO_CLONE_URL="https://gitea.mixinet.net/mixinet/blogops.git"
MAIL_PREFIX="[BLOGOPS-WEBHOOK] "
# Address that gets all messages, leave it empty if not wanted
MAIL_TO_ADDR="blogops@mixinet.net"
# If the following variable is set to 'true' the pusher gets mail on failures
MAIL_ERRFILE="false"
# If the following variable is set to 'true' the pusher gets mail on success
MAIL_LOGFILE="false"
# gitea's conf/app.ini value of NO_REPLY_ADDRESS, it is used for email domains
# when the KeepEmailPrivate option is enabled for a user
NO_REPLY_ADDRESS="noreply.example.org"
# Directories
BASE_DIR="/srv/blogops"
PUBLIC_DIR="$BASE_DIR/public"
NGINX_BASE_DIR="$BASE_DIR/nginx"
PUBLIC_HTML_DIR="$NGINX_BASE_DIR/public_html"
WEBHOOK_BASE_DIR="$BASE_DIR/webhook"
WEBHOOK_SPOOL_DIR="$WEBHOOK_BASE_DIR/spool"
WEBHOOK_ACCEPTED="$WEBHOOK_SPOOL_DIR/accepted"
WEBHOOK_DEPLOYED="$WEBHOOK_SPOOL_DIR/deployed"
WEBHOOK_REJECTED="$WEBHOOK_SPOOL_DIR/rejected"
WEBHOOK_TROUBLED="$WEBHOOK_SPOOL_DIR/troubled"
WEBHOOK_LOG_DIR="$WEBHOOK_SPOOL_DIR/log"
# Files
TODAY="$(date +%Y%m%d)"
OUTPUT_BASENAME="$(date +%Y%m%d-%H%M%S.%N)"
WEBHOOK_LOGFILE_PATH="$WEBHOOK_LOG_DIR/$OUTPUT_BASENAME.log"
WEBHOOK_ACCEPTED_JSON="$WEBHOOK_ACCEPTED/$OUTPUT_BASENAME.json"
WEBHOOK_ACCEPTED_LOGF="$WEBHOOK_ACCEPTED/$OUTPUT_BASENAME.log"
WEBHOOK_REJECTED_TODAY="$WEBHOOK_REJECTED/$TODAY"
WEBHOOK_REJECTED_JSON="$WEBHOOK_REJECTED_TODAY/$OUTPUT_BASENAME.json"
WEBHOOK_REJECTED_LOGF="$WEBHOOK_REJECTED_TODAY/$OUTPUT_BASENAME.log"
WEBHOOK_DEPLOYED_TODAY="$WEBHOOK_DEPLOYED/$TODAY"
WEBHOOK_DEPLOYED_JSON="$WEBHOOK_DEPLOYED_TODAY/$OUTPUT_BASENAME.json"
WEBHOOK_DEPLOYED_LOGF="$WEBHOOK_DEPLOYED_TODAY/$OUTPUT_BASENAME.log"
WEBHOOK_TROUBLED_TODAY="$WEBHOOK_TROUBLED/$TODAY"
WEBHOOK_TROUBLED_JSON="$WEBHOOK_TROUBLED_TODAY/$OUTPUT_BASENAME.json"
WEBHOOK_TROUBLED_LOGF="$WEBHOOK_TROUBLED_TODAY/$OUTPUT_BASENAME.log"
# Query to get variables from a gitea webhook json
ENV_VARS_QUERY="$(
printf "%s" \
'(. @sh "gt_ref=\(.ref);"),' \
'(. @sh "gt_after=\(.after);"),' \
'(.repository @sh "gt_repo_clone_url=\(.clone_url);"),' \
'(.repository @sh "gt_repo_name=\(.name);"),' \
'(.pusher @sh "gt_pusher_full_name=\(.full_name);"),' \
'(.pusher @sh "gt_pusher_email=\(.email);")'
)"
# ---------
# Functions
# ---------
webhook_log()
echo "$(date -R) $*" >>"$WEBHOOK_LOGFILE_PATH"
webhook_check_directories()
for _d in "$WEBHOOK_SPOOL_DIR" "$WEBHOOK_ACCEPTED" "$WEBHOOK_DEPLOYED" \
"$WEBHOOK_REJECTED" "$WEBHOOK_TROUBLED" "$WEBHOOK_LOG_DIR"; do
[ -d "$_d" ] mkdir "$_d"
done
webhook_clean_directories()
# Try to remove empty dirs
for _d in "$WEBHOOK_ACCEPTED" "$WEBHOOK_DEPLOYED" "$WEBHOOK_REJECTED" \
"$WEBHOOK_TROUBLED" "$WEBHOOK_LOG_DIR" "$WEBHOOK_SPOOL_DIR"; do
if [ -d "$_d" ]; then
rmdir "$_d" 2>/dev/null true
fi
done
webhook_accept()
webhook_log "Accepted: $*"
mv "$WEBHOOK_JSON_INPUT_FILE" "$WEBHOOK_ACCEPTED_JSON"
mv "$WEBHOOK_LOGFILE_PATH" "$WEBHOOK_ACCEPTED_LOGF"
WEBHOOK_LOGFILE_PATH="$WEBHOOK_ACCEPTED_LOGF"
webhook_reject()
[ -d "$WEBHOOK_REJECTED_TODAY" ] mkdir "$WEBHOOK_REJECTED_TODAY"
webhook_log "Rejected: $*"
if [ -f "$WEBHOOK_JSON_INPUT_FILE" ]; then
mv "$WEBHOOK_JSON_INPUT_FILE" "$WEBHOOK_REJECTED_JSON"
fi
mv "$WEBHOOK_LOGFILE_PATH" "$WEBHOOK_REJECTED_LOGF"
exit 0
webhook_deployed()
[ -d "$WEBHOOK_DEPLOYED_TODAY" ] mkdir "$WEBHOOK_DEPLOYED_TODAY"
webhook_log "Deployed: $*"
mv "$WEBHOOK_ACCEPTED_JSON" "$WEBHOOK_DEPLOYED_JSON"
mv "$WEBHOOK_ACCEPTED_LOGF" "$WEBHOOK_DEPLOYED_LOGF"
WEBHOOK_LOGFILE_PATH="$WEBHOOK_DEPLOYED_LOGF"
webhook_troubled()
[ -d "$WEBHOOK_TROUBLED_TODAY" ] mkdir "$WEBHOOK_TROUBLED_TODAY"
webhook_log "Troubled: $*"
mv "$WEBHOOK_ACCEPTED_JSON" "$WEBHOOK_TROUBLED_JSON"
mv "$WEBHOOK_ACCEPTED_LOGF" "$WEBHOOK_TROUBLED_LOGF"
WEBHOOK_LOGFILE_PATH="$WEBHOOK_TROUBLED_LOGF"
print_mailto()
_addr="$1"
_user_email=""
# Add the pusher email address unless it is from the domain NO_REPLY_ADDRESS,
# which should match the value of that variable on the gitea 'app.ini' (it
# is the domain used for emails when the user hides it).
# shellcheck disable=SC2154
if [ -n "$ gt_pusher_email##*@"$ NO_REPLY_ADDRESS " " ] &&
[ -z "$ gt_pusher_email##*@* " ]; then
_user_email="\"$gt_pusher_full_name <$gt_pusher_email>\""
fi
if [ "$_addr" ] && [ "$_user_email" ]; then
echo "$_addr,$_user_email"
elif [ "$_user_email" ]; then
echo "$_user_email"
elif [ "$_addr" ]; then
echo "$_addr"
fi
mail_success()
to_addr="$MAIL_TO_ADDR"
if [ "$MAIL_LOGFILE" = "true" ]; then
to_addr="$(print_mailto "$to_addr")"
fi
if [ "$to_addr" ]; then
# shellcheck disable=SC2154
subject="OK - $gt_repo_name updated to commit '$gt_after'"
mail -s "$ MAIL_PREFIX $ subject " "$to_addr" \
<"$WEBHOOK_LOGFILE_PATH"
fi
mail_failure()
to_addr="$MAIL_TO_ADDR"
if [ "$MAIL_ERRFILE" = true ]; then
to_addr="$(print_mailto "$to_addr")"
fi
if [ "$to_addr" ]; then
# shellcheck disable=SC2154
subject="KO - $gt_repo_name update FAILED for commit '$gt_after'"
mail -s "$ MAIL_PREFIX $ subject " "$to_addr" \
<"$WEBHOOK_LOGFILE_PATH"
fi
# ----
# MAIN
# ----
# Check directories
webhook_check_directories
# Go to the base directory
cd "$BASE_DIR"
# Check if the file exists
WEBHOOK_JSON_INPUT_FILE="$1"
if [ ! -f "$WEBHOOK_JSON_INPUT_FILE" ]; then
webhook_reject "Input arg '$1' is not a file, aborting"
fi
# Parse the file
webhook_log "Processing file '$WEBHOOK_JSON_INPUT_FILE'"
eval "$(jq -r "$ENV_VARS_QUERY" "$WEBHOOK_JSON_INPUT_FILE")"
# Check that the repository clone url is right
# shellcheck disable=SC2154
if [ "$gt_repo_clone_url" != "$REPO_CLONE_URL" ]; then
webhook_reject "Wrong repository: '$gt_clone_url'"
fi
# Check that the branch is the right one
# shellcheck disable=SC2154
if [ "$gt_ref" != "$REPO_REF" ]; then
webhook_reject "Wrong repository ref: '$gt_ref'"
fi
# Accept the file
# shellcheck disable=SC2154
webhook_accept "Processing '$gt_repo_name'"
# Update the checkout
ret="0"
git fetch >>"$WEBHOOK_LOGFILE_PATH" 2>&1 ret="$?"
if [ "$ret" -ne "0" ]; then
webhook_troubled "Repository fetch failed"
mail_failure
fi
# shellcheck disable=SC2154
git checkout "$gt_after" >>"$WEBHOOK_LOGFILE_PATH" 2>&1 ret="$?"
if [ "$ret" -ne "0" ]; then
webhook_troubled "Repository checkout failed"
mail_failure
fi
# Remove the build dir if present
if [ -d "$PUBLIC_DIR" ]; then
rm -rf "$PUBLIC_DIR"
fi
# Build site
docker compose run hugo -- >>"$WEBHOOK_LOGFILE_PATH" 2>&1 ret="$?"
# go back to the main branch
git switch main && git pull
# Fail if public dir was missing
if [ "$ret" -ne "0" ] [ ! -d "$PUBLIC_DIR" ]; then
webhook_troubled "Site build failed"
mail_failure
fi
# Remove old public_html copies
webhook_log 'Removing old site versions, if present'
find $NGINX_BASE_DIR -mindepth 1 -maxdepth 1 -name 'public_html-*' -type d \
-exec rm -rf \; >>"$WEBHOOK_LOGFILE_PATH" 2>&1 ret="$?"
if [ "$ret" -ne "0" ]; then
webhook_troubled "Removal of old site versions failed"
mail_failure
fi
# Switch site directory
TS="$(date +%Y%m%d-%H%M%S)"
if [ -d "$PUBLIC_HTML_DIR" ]; then
webhook_log "Moving '$PUBLIC_HTML_DIR' to '$PUBLIC_HTML_DIR-$TS'"
mv "$PUBLIC_HTML_DIR" "$PUBLIC_HTML_DIR-$TS" >>"$WEBHOOK_LOGFILE_PATH" 2>&1
ret="$?"
fi
if [ "$ret" -eq "0" ]; then
webhook_log "Moving '$PUBLIC_DIR' to '$PUBLIC_HTML_DIR'"
mv "$PUBLIC_DIR" "$PUBLIC_HTML_DIR" >>"$WEBHOOK_LOGFILE_PATH" 2>&1
ret="$?"
fi
if [ "$ret" -ne "0" ]; then
webhook_troubled "Site switch failed"
mail_failure
else
webhook_deployed "Site deployed successfully"
mail_success
fi
# ----
# vim: ts=2:sw=2:et:ai:sts=2 One month ago I started work on a new side project which is now up and running, and deserving on an introductory blog post: r2u. It was announced in two earlier tweets (first, second) which contained the two (wicked) demos below also found at the documentation site.
So what is this about? It brings full and complete CRAN installability to Ubuntu LTS, both the focal release 20.04 and the recent jammy release 22.04. It is unique in resolving all R and CRAN packages with the system package manager. So whenever you install something it is guaranteed to run as its dependencies are resolved and co-installed as needed. Equally important, no shared library will be updated or removed by the system as the possible dependency of the R package is known and declared. No other package management system for R does that as only
One month ago I started work on a new side project which is now up and running, and deserving on an introductory blog post: r2u. It was announced in two earlier tweets (first, second) which contained the two (wicked) demos below also found at the documentation site.
So what is this about? It brings full and complete CRAN installability to Ubuntu LTS, both the focal release 20.04 and the recent jammy release 22.04. It is unique in resolving all R and CRAN packages with the system package manager. So whenever you install something it is guaranteed to run as its dependencies are resolved and co-installed as needed. Equally important, no shared library will be updated or removed by the system as the possible dependency of the R package is known and declared. No other package management system for R does that as only apt on Debian or Ubuntu can and this project integrates all CRAN packages (plus 200+ BioConductor packages). It will work with any Ubuntu installation on laptop, desktop, server, cloud, container, or in WSL2 (but is limited to Intel/AMD chips, sorry Raspberry Pi or M1 laptop). It covers all of CRAN (or nearly 19k packages), all the BioConductor packages depended-upon (currently over 200), and only excludes less than a handful of CRAN packages that cannot be built.
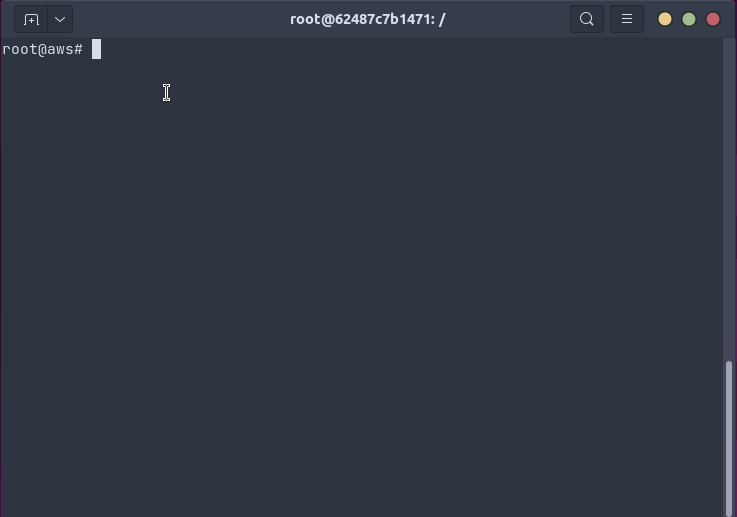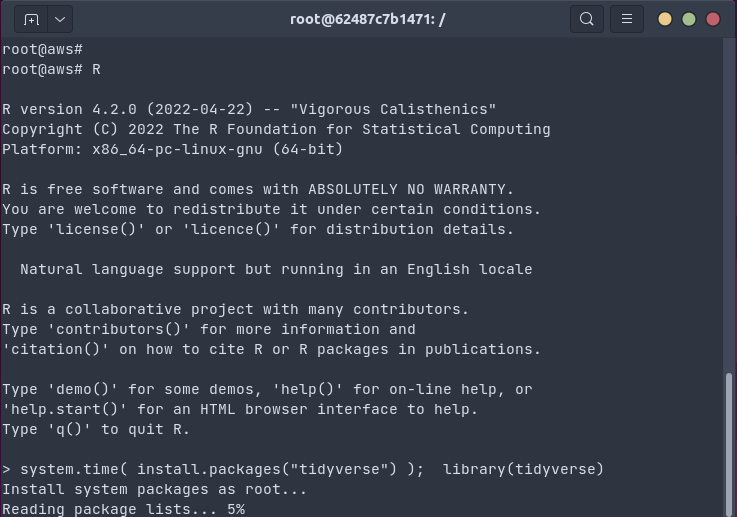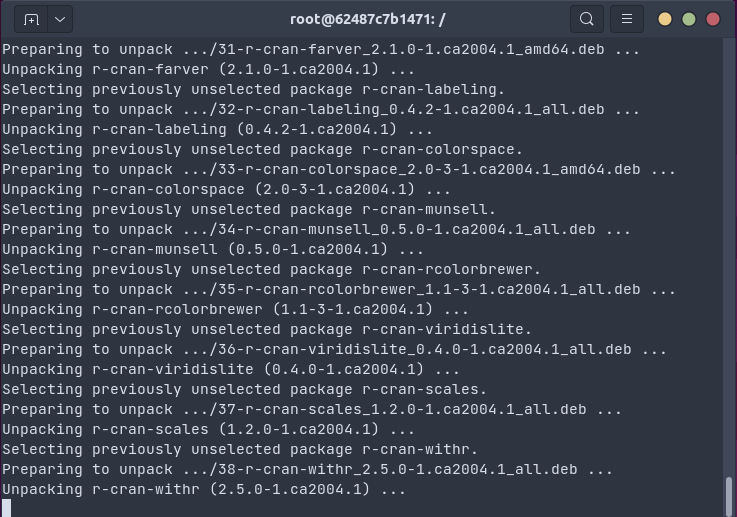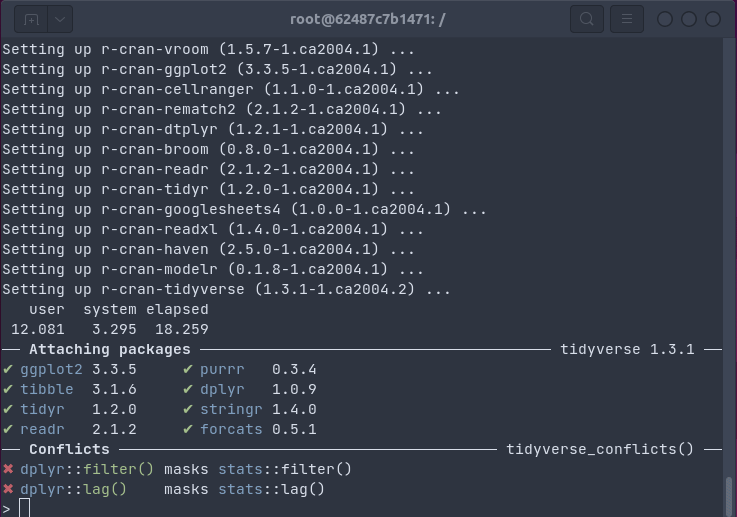
bspm
The r2u setup can be used directly with apt (or dpkg or any other frontend to the package management system). Once installed apt update; apt upgrade will take care of new packages. For this to work, all CRAN packages (and all BioConductor packages depended upon) are mapped to names like r-cran-rcpp and r-bioc-s4vectors: an r prefix, the repo, and the package name, all lower-cased. That works but thanks to the wonderful bspm package by I aki car we can do much better. It connects R s own install.packages() and update.packages() to apt. So we can just say (as the demos above show) install.packages("tidyverse") or install.packages("brms") and binaries are installed via apt which is fantastic and it connects R to the system package manager. The setup is really only two lines and described at the r2u site as part of the setup.
This post by Dirk Eddelbuettel originated on his Thinking inside the box blog. Please report excessive re-aggregation in third-party for-profit settings.
Needs to be able to create two copies always. Can get stuck in irreversible read-only mode if only one copy can be made.Even as of now, RAID-1 and RAID-10 has this note:
The simple redundancy RAID levels utilize different mirrors in a way that does not achieve the maximum performance. The logic can be improved so the reads will spread over the mirrors evenly or based on device congestion.Granted, that's not a stability concern anymore, just performance. A reviewer of a draft of this article actually claimed that BTRFS only reads from one of the drives, which hopefully is inaccurate, but goes to show how confusing all this is. There are other warnings in the Debian wiki that are quite scary. Even the legendary Arch wiki has a warning on top of their BTRFS page, still. Even if those issues are now fixed, it can be hard to tell when they were fixed. There is a changelog by feature but it explicitly warns that it doesn't know "which kernel version it is considered mature enough for production use", so it's also useless for this. It would have been much better if BTRFS was released into the world only when those bugs were being completely fixed. Or that, at least, features were announced when they were stable, not just "we merged to mainline, good luck". Even now, we get mixed messages even in the official BTRFS documentation which says "The Btrfs code base is stable" (main page) while at the same time clearly stating unstable parts in the status page (currently RAID56). There are much harsher BTRFS critics than me out there so I will stop here, but let's just say that I feel a little uncomfortable trusting server data with full RAID arrays to BTRFS. But surely, for a workstation, things should just work smoothly... Right? Well, let's see the snags I hit.
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
sda 8:0 0 931,5G 0 disk
sda1 8:1 0 200M 0 part /boot/efi
sda2 8:2 0 1G 0 part /boot
sda3 8:3 0 7,8G 0 part
fedora_swap 253:5 0 7.8G 0 crypt [SWAP]
sda4 8:4 0 922,5G 0 part
fedora_crypt 253:4 0 922,5G 0 crypt /
/dev/nvme0n1 and nvme1n1/dev/md1vg_tbbuild05 (multiple PVs can be added to a single VG which is
why there is that abstraction)NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
nvme0n1 259:0 0 1.7T 0 disk
nvme0n1p1 259:1 0 8M 0 part
nvme0n1p2 259:2 0 512M 0 part
md0 9:0 0 511M 0 raid1 /boot
nvme0n1p3 259:3 0 1.7T 0 part
md1 9:1 0 1.7T 0 raid1
crypt_dev_md1 253:0 0 1.7T 0 crypt
vg_tbbuild05-root 253:1 0 30G 0 lvm /
vg_tbbuild05-swap 253:2 0 125.7G 0 lvm [SWAP]
vg_tbbuild05-srv 253:3 0 1.5T 0 lvm /srv
nvme0n1p4 259:4 0 1M 0 part
nvme1n1 disk because it's basically the same.
Now, if we look at my BTRFS-enabled workstation, which doesn't even
have RAID, we have the following:
/dev/sda with, again, /dev/sda4 being where BTRFS livesfedora_crypt, which is, confusingly, kind of like a
volume group. it's where everything lives. i think.home, root, /, etc. those are actually the things
that get mounted. you'd think you'd mount a filesystem, but no, you
mount a subvolume. that is backwards.lsblk:
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
sda 8:0 0 931,5G 0 disk
sda1 8:1 0 200M 0 part /boot/efi
sda2 8:2 0 1G 0 part /boot
sda3 8:3 0 7,8G 0 part [SWAP]
sda4 8:4 0 922,5G 0 part
fedora_crypt 253:4 0 922,5G 0 crypt /srv
lsblk definitely gets
confused here. I frankly don't quite understand what's going on, even
after repeatedly looking around the rather dismal
documentation. But that's what I gather from the following
commands:
root@curie:/home/anarcat# btrfs filesystem show
Label: 'fedora' uuid: 5abb9def-c725-44ef-a45e-d72657803f37
Total devices 1 FS bytes used 883.29GiB
devid 1 size 922.47GiB used 916.47GiB path /dev/mapper/fedora_crypt
root@curie:/home/anarcat# btrfs subvolume list /srv
ID 257 gen 108092 top level 5 path home
ID 258 gen 108094 top level 5 path root
ID 263 gen 108020 top level 258 path root/var/lib/machines
filesystem show, I
fail:
root@curie:/home/anarcat# btrfs subvolume list /dev/mapper/fedora_crypt
ERROR: not a btrfs filesystem: /dev/mapper/fedora_crypt
ERROR: can't access '/dev/mapper/fedora_crypt'
root@curie:/home/anarcat# btrfs subvolume list fedora
ERROR: cannot access 'fedora': No such file or directory
ERROR: can't access 'fedora'
btrfs commandline, as I surely will. I
will possibly even update this section as I get better at it, or based
on my reader's judicious feedback.
/etc/fstab,
on the Debian side of things:
UUID=5abb9def-c725-44ef-a45e-d72657803f37 /srv btrfs defaults 0 2
mount tells me that's actually the "root" (? /?)
subvolume:
root@curie:/home/anarcat# mount grep /srv
/dev/mapper/fedora_crypt on /srv type btrfs (rw,relatime,space_cache,subvolid=5,subvol=/)
subvolume list showed I had home, root, and
var/lib/machines. Let's try root:
mount -o subvol=root /dev/mapper/fedora_crypt /mnt
root is not the same as /, it's a different
subvolume! It seems to be the Fedora root (/, really) filesystem. No
idea what is happening here. I also have a home subvolume, let's
mount it too, for good measure:
mount -o subvol=home /dev/mapper/fedora_crypt /mnt/home
lsblk doesn't notice those two new mountpoints, and that's
normal: it only lists block devices and subvolumes (rather
inconveniently, I'd say) do not show up as devices:
root@curie:/home/anarcat# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
sda 8:0 0 931,5G 0 disk
sda1 8:1 0 200M 0 part
sda2 8:2 0 1G 0 part
sda3 8:3 0 7,8G 0 part
sda4 8:4 0 922,5G 0 part
fedora_crypt 253:4 0 922,5G 0 crypt /srv
root@curie:/home/anarcat# df -h /srv /mnt /mnt/home
Filesystem Size Used Avail Use% Mounted on
/dev/mapper/fedora_crypt 923G 886G 31G 97% /srv
/dev/mapper/fedora_crypt 923G 886G 31G 97% /mnt
/dev/mapper/fedora_crypt 923G 886G 31G 97% /mnt/home
/srv and /mnt
(and /mnt/home?!) to be exactly the same, but no: they are entirely
different directory structures, which I will not call "filesystems"
here because everyone's head will explode in sparks of confusion.)
Yes, disk space is shared (that's the Size and Avail columns,
makes sense). But nope, no cookie for you: they all have the same
Used columns, so you need to actually walk the entire filesystem to
figure out what each disk takes.
(For future reference, that's basically:
root@curie:/home/anarcat# time du -schx /mnt/home /mnt /srv
124M /mnt/home
7.5G /mnt
875G /srv
883G total
real 2m49.080s
user 0m3.664s
sys 0m19.013s
root@tubman:~# time df -t zfs -h
Filesystem Size Used Avail Use% Mounted on
rpool/ROOT/debian 3.5T 1.4G 3.5T 1% /
rpool/var/tmp 3.5T 384K 3.5T 1% /var/tmp
rpool/var/spool 3.5T 256K 3.5T 1% /var/spool
rpool/var/log 3.5T 2.0G 3.5T 1% /var/log
rpool/home/root 3.5T 2.2G 3.5T 1% /root
rpool/home 3.5T 256K 3.5T 1% /home
rpool/srv 3.5T 80G 3.5T 3% /srv
rpool/var/cache 3.5T 114M 3.5T 1% /var/cache
bpool/BOOT/debian 571M 90M 481M 16% /boot
real 0m0.003s
user 0m0.002s
sys 0m0.000s
df does with BTRFS filesystems, the
btrfs filesystem usage command:
root@curie:/home/anarcat# time btrfs filesystem usage /srv
Overall:
Device size: 922.47GiB
Device allocated: 916.47GiB
Device unallocated: 6.00GiB
Device missing: 0.00B
Used: 884.97GiB
Free (estimated): 30.84GiB (min: 27.84GiB)
Free (statfs, df): 30.84GiB
Data ratio: 1.00
Metadata ratio: 2.00
Global reserve: 512.00MiB (used: 0.00B)
Multiple profiles: no
Data,single: Size:906.45GiB, Used:881.61GiB (97.26%)
/dev/mapper/fedora_crypt 906.45GiB
Metadata,DUP: Size:5.00GiB, Used:1.68GiB (33.58%)
/dev/mapper/fedora_crypt 10.00GiB
System,DUP: Size:8.00MiB, Used:128.00KiB (1.56%)
/dev/mapper/fedora_crypt 16.00MiB
Unallocated:
/dev/mapper/fedora_crypt 6.00GiB
real 0m0,004s
user 0m0,000s
sys 0m0,004s
filesystem usage, not
subvolume usage, which unhelpfully refuses to exist. That command
only shows that one "filesystem" internal statistics that are pretty
opaque.. You can also appreciate that it's wasting 6GB of
"unallocated" disk space there: I probably did something Very Wrong
and should be punished by Hacker News. I also wonder why it has 1.68GB
of "metadata" used...
At this point, I just really want to throw that thing out of the
window and restart from scratch. I don't really feel like learning the
BTRFS internals, as they seem oblique and completely bizarre to me. It
feels a little like the state of PHP now: it's actually pretty solid,
but built upon so many layers of cruft that I still feel it corrupts
my brain every time I have to deal with it (needle or haystack first?
anyone?)...
 Previously: v5.9
Linux v5.10 was released in December, 2020. Here s my summary of various security things that I found interesting:
AMD SEV-ES
Previously: v5.9
Linux v5.10 was released in December, 2020. Here s my summary of various security things that I found interesting:
AMD SEV-ESif/else choice can be hard-coded, instead of being run-time evaluated every time. Such branches can be updated too (the kernel just rewrites the code to switch around the branch ). All these principles apply to static calls as well, but they re for replacing indirect function calls (i.e. a call through a function pointer) with a direct call (i.e. a hard-coded call address). This eliminates the need for Spectre mitigations (e.g. RETPOLINE) for these indirect calls, and avoids a memory lookup for the pointer. For hot-path code (like the scheduler), this has a measurable performance impact. It also serves as a kind of Control Flow Integrity implementation: an indirect call got removed, and the potential destinations have been explicitly identified at compile-time.
network RNG improvementsCAP_SETGID (instead of to just any group), providing a way to keep the power of granting this capability much more limited. (This isn t complete yet, though, since handling setgroups() is still needed.)
improve kernel s internal checking of file contentsset_fs(), Christoph Hellwig made it possible for set_fs() to be optional for an architecture. Subsequently, he then removed set_fs() entirely for x86, riscv, and powerpc. These architectures will now be free from the entire class of kernel address limit attacks that only needed to corrupt a single value in struct thead_info.
sysfs_emit() replaces sprintf() in /syssprintf() and snprintf() in /sys handlers by creating a new helper, sysfs_emit(). This will handle the cases where kernel code was not correctly dealing with the length results from sprintf() calls, which might lead to buffer overflows in the PAGE_SIZE buffer that /sys handlers operate on. With the helper in place, it was possible to start the refactoring of the many sprintf() callers.
nosymfollow mount optionnosymfollow mount option. This entirely disables symlink resolution for the given filesystem, similar to other mount options where noexec disallows execve(), nosuid disallows setid bits, and nodev disallows device files. Quoting the patch, it is useful as a defensive measure for systems that need to deal with untrusted file systems in privileged contexts. (i.e. for when /proc/sys/fs/protected_symlinks isn t a big enough hammer.) Chrome OS uses this option for its stateful filesystem, as symlink traversal as been a common attack-persistence vector.
ARMv8.5 Memory Tagging Extension support-Warray-bounds compiler flag and clear the path for saner bounds checking of array indexes and memcpy() usage.
That s it for now! Please let me know if you think anything else needs some attention. Next up is Linux v5.11.
2022, Kees Cook. This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 License.
debian/changelog at least:
procmail (3.22-1) unstable; urgency=low
* New upstream release, which uses the standard' format for Maildir
filenames and retries on name collision. It also contains some
bug fixes from the 3.23pre snapshot dated 2001-09-13.
* Removed sendmail' from the Recommends field, since we already
have exim' (the default Debian MTA) and mail-transport-agent'.
* Removed suidmanager support. Conflicts: suidmanager (<< 0.50).
* Added support for DEB_BUILD_OPTIONS in the source package.
* README.Maildir: Do not use locking on the example recipe,
since it's wrong to do so in this case.
-- Santiago Vila <sanvila@debian.org> Wed, 21 Nov 2001 09:40:20 +0100
root:mail in
Debian. There's no debconf or pre-seed setting that can change
this. There has been two bug reports against the Debian to make this
configurable (298058, 264011), but both were closed to say
that, basically, you should use dpkg-statoverride to change the
permissions on the binary.
So if anything, you should immediately run this command on any host
that you have procmail installed on:
dpkg-statoverride --update --add root root 0755 /usr/bin/procmail
Executive summary: delete the procmail port; the code is not safe and should not be used as a basis for any further work.I just read some of the code again this morning, after the original author claimed that procmail was active again. It's still littered with bizarre macros like:
#define bit_set(name,which,value) \
(value?(name[bit_index(which)] =bit_mask(which)):\
(name[bit_index(which)]&=~bit_mask(which)))
#define jj (aleps.au.sopc)
strcpy extensively. malloc()
is thrown around gotos like it's 1984 all over again. (To be fair,
it has been feeling like 1984 a lot lately, but that's another matter
entirely.)
That null pointer deref bug? It's fixed upstream now, in this
commit merged a few hours ago, which I presume might be in response
to my request to remove procmail from Debian.
So while that's nice, this is the just tip of the iceberg. I speculate
that one could easily find an exploitable crash in procmail if only by
running it through a fuzzer. But I don't need to speculate: procmail
had, for years, serious security issues that could possibly lead to
root privilege escalation, remotely exploitable if procmail is (as
it's designed to do) exposed to the network.
Maybe I'm overreacting. Maybe the procmail author will go through the
code base and do a proper rewrite. But I don't think that's what is in
the cards right now. What I expect will happen next is that people
will start fuzzing procmail, throw an uncountable number of bug
reports at it which will get fixed in a trickle while never fixing the
underlying, serious design flaws behind procmail.
procmail(1) itself are typically part of mail
servers. For example, Dovecot has its own LDA which implements
the standard Sieve language (RFC 5228). (Interestingly, Sieve
was published as RFC 3028 in 2001, before procmail was formally
abandoned.)
Courier also has "maildrop" which has its own filtering mechanism,
and there is fdm (2007) which is a fetchmail and procmail
replacement. Update: there's also mailprocessing, which is not
an LDA, but processing an existing folder. It was, however,
specifically designed to replace complex Procmail rules.
But procmail, of course, doesn't just ship procmail; that would just
be too easy. It ships mailstat(1) which we could probably ignore
because it only parses procmail log files. But more importantly, it
also ships:
lockfile(1) - conditional semaphore-file creatorformail(1) - mail (re)formatterlockfile(1) already has a somewhat acceptable replacement in the form of
flock(1), part of util-linux (which is Essential, so installed on
any normal Debian system). It might not be a direct drop-in
replacement, but it should be close enough.
formail(1) is similar: the courier maildrop package ships
reformail(1) which is, presumably, a rewrite of formail. It's
unclear if it's a drop-in replacement, but it should probably possible
to port uses of formail to it easily.
Update: theThe real challenge is, of course, migrating those oldmaildroppackage ships a SUID root binary (two, even). So if you want onlyreformail(1), you might want to disable that with:It would be perhaps better to havedpkg-statoverride --update --add root root 0755 /usr/bin/lockmail.maildrop dpkg-statoverride --update --add root root 0755 /usr/bin/maildropreformail(1)as a separate package, see bug 1006903 for that discussion.
.procmailrc
recipes to Sieve (basically). I added a few examples in the appendix
below. You might notice the Sieve examples are easier to read, which
is a nice added bonus.
procmail
installed everywhere, possibly because userdir-ldap was using
it for lockfile until 2019. I sent a patch to fix that and scrambled
to remove get rid of procmail everywhere. That took about a day.
But many other sites are now in that situation, possibly not imagining
they have this glaring security hole in their infrastructure.
~/.dovecot.sieve.
user+foo@example.com to the folder
foo. You might write something like this in procmail:
MAILDIR=$HOME/Maildir/
DEFAULT=$MAILDIR
LOGFILE=$HOME/.procmail.log
VERBOSE=off
EXTENSION=$1 # Need to rename it - ?? does not like $1 nor 1
:0
* EXTENSION ?? [a-zA-Z0-9]+
.$EXTENSION/
require ["variables", "envelope", "fileinto", "subaddress"];
########################################################################
# wildcard +extension
# https://doc.dovecot.org/configuration_manual/sieve/examples/#plus-addressed-mail-filtering
if envelope :matches :detail "to" "*"
# Save name in $ name in all lowercase
set :lower "name" "$ 1 ";
fileinto "$ name ";
stop;
Subject: line having FreshPorts
in it into the freshports folder, and mails from alternc.org
mailing lists into the alternc folder:
:0
## mailing list freshports
* ^Subject.*FreshPorts.*
.freshports/
:0
## mailing list alternc
* ^List-Post.*mailto:.*@alternc.org.*
.alternc/
if header :contains "subject" "FreshPorts"
fileinto "freshports";
elsif header :contains "List-Id" "alternc.org"
fileinto "alternc";
:0
* ^Subject: Cron
* ^From: .*root@
.rapports/
if header :comparator "i;octet" :contains "Subject" "Cron"
if header :regex :comparator "i;octet" "From" ".*root@"
fileinto "rapports";
if header :contains "Precedence" "bulk"
fileinto "bulk";
if exists "List-Id"
fileinto "lists";
if anyof (header :contains "from" "example.com",
header :contains ["to", "cc"] "anarcat@example.com")
fileinto "example";
if anyof (exists "X-Cron-Env",
header :contains ["subject"] ["security run output",
"monthly run output",
"daily run output",
"weekly run output",
"Debian Package Updates",
"Debian package update",
"daily mail stats",
"Anacron job",
"nagios",
"changes report",
"run output",
"[Systraq]",
"Undelivered mail",
"Postfix SMTP server: errors from",
"backupninja",
"DenyHosts report",
"Debian security status",
"apt-listchanges"
],
header :contains "Auto-Submitted" "auto-generated",
envelope :contains "from" ["nagios@",
"logcheck@",
"root@"])
fileinto "rapports";
 Welcome to the December 2021 report from the Reproducible Builds project! In these reports, we try and summarise what we have been up to over the past month, as well as what else has been occurring in the world of software supply-chain security.
As a quick recap of what reproducible builds is trying to address, whilst anyone may inspect the source code of free software for malicious flaws, almost all software is distributed to end users as pre-compiled binaries. The motivation behind the reproducible builds effort is to ensure no flaws have been introduced during this compilation process by promising identical results are always generated from a given source, thus allowing multiple third-parties to come to a consensus on whether a build was compromised. As always, if you would like to contribute to the project, please get in touch with us directly or visit the Contribute page on our website.
Welcome to the December 2021 report from the Reproducible Builds project! In these reports, we try and summarise what we have been up to over the past month, as well as what else has been occurring in the world of software supply-chain security.
As a quick recap of what reproducible builds is trying to address, whilst anyone may inspect the source code of free software for malicious flaws, almost all software is distributed to end users as pre-compiled binaries. The motivation behind the reproducible builds effort is to ensure no flaws have been introduced during this compilation process by promising identical results are always generated from a given source, thus allowing multiple third-parties to come to a consensus on whether a build was compromised. As always, if you would like to contribute to the project, please get in touch with us directly or visit the Contribute page on our website.
 Early in December, Julien Voisin blogged about setting up a rebuilderd instance in order to reproduce Tails images. Working on previous work from 2018, Julien has now set up a public-facing instance which is providing build attestations.
As Julien dryly notes in his post, Currently, this isn t really super-useful to anyone, except maybe some Tails developers who want to check that the release manager didn t backdoor the released image. Naturally, we would contend sincerely that this is indeed useful.
Early in December, Julien Voisin blogged about setting up a rebuilderd instance in order to reproduce Tails images. Working on previous work from 2018, Julien has now set up a public-facing instance which is providing build attestations.
As Julien dryly notes in his post, Currently, this isn t really super-useful to anyone, except maybe some Tails developers who want to check that the release manager didn t backdoor the released image. Naturally, we would contend sincerely that this is indeed useful.
0.4.7.3-alpha of Tor can now build reproducible tarballs via the make dist-reprod command. This issue was tracked via Tor issue #26299.
mkimg and makefs commands:
Fabian s original post generated a short back-and-forth with Chris Lamb regarding how diffoscope might be able to support the particular format of images generated by this command set.After rebasing ElectroBSD from FreeBSD stable/11 to stable/12
I recently noticed that the "memstick" images are unfortunately
still not 100% reproducible.
 diffoscope is our in-depth and content-aware diff utility. Not only can it locate and diagnose reproducibility issues, it can provide human-readable diffs from many kinds of binary formats. This month, Chris Lamb prepared and uploading versions
diffoscope is our in-depth and content-aware diff utility. Not only can it locate and diagnose reproducibility issues, it can provide human-readable diffs from many kinds of binary formats. This month, Chris Lamb prepared and uploading versions 195, 196, 197 and 198 to Debian, as well as made the following changes:
.dsc field values. [ ]/usr/lib/x86_64-linux-gnu to our local binary search path. [ ]has_same_content_as logging calls. [ ]token variable with an anonymously-named variable instead to remove extra lines. [ ].pyc files. This fixes test failures on big-endian machines. [ ]binary-with-bad-dynamic-table. [ ]Enhances field in debian/control. [ ]GNU_BUILD_ID field has been modified [ ]. Thank you for your contributions!
 In Debian this month, 70 reviews of packages were added, 27 were updated and 41 were removed, adding to our database of knowledge about specific issues. A number of issue types were created as well, including:
In Debian this month, 70 reviews of packages were added, 27 were updated and 41 were removed, adding to our database of knowledge about specific issues. A number of issue types were created as well, including:
build_path_identifiers_in_documentation_generated_by_doxygennon_deterministic_doc_base_file_for_javadocnondeterministic_ordering_in_guile_binaries1.13.0-1 was uploaded to Debian unstable by Holger Levsen. It included contributions already covered in previous months as well as new ones from Mattia Rizzolo, particularly that the dh_strip_nondeterminism Debian integration interface uses the new get_non_binnmu_date_epoch() utility when available: this is important to ensure that strip-nondeterminism does not break some kinds of binNMUs.
 In the world of openSUSE, however, Bernhard M. Wiedemann posted his monthly reproducible builds status report.
In the world of openSUSE, however, Bernhard M. Wiedemann posted his monthly reproducible builds status report.
 In NixOS, work towards the longer-term goal of making the graphical installation image reproducible is ongoing. For example, Artturin made the
In NixOS, work towards the longer-term goal of making the graphical installation image reproducible is ongoing. For example, Artturin made the gnome-desktop package reproducible.
g++7/rsync (randomness in output)python-eventlet (build fails in the future)python-PyQRCode (incorporates copyright year)apbs.binutils-riscv64-unknown-elf.gcc-riscv64-unknown-elf.userbindmount.nanomsg.freediameter.gr-satellites.kjs.xeus-python.libime.fcitx5-gtk.fcitx.libpodofo.meshlab.eiskaltdcpp.editorconfig-core.python-parse-type.sphinx-copybutton.fcitx5-qt.libxmlb, fixed by Richard Hughes. Waiting for an upstream release. The Reproducible Builds project runs a significant testing framework at tests.reproducible-builds.org, to check packages and other artifacts for reproducibility. This month, the following changes were made:
The Reproducible Builds project runs a significant testing framework at tests.reproducible-builds.org, to check packages and other artifacts for reproducibility. This month, the following changes were made:
/boot partition size. [ ]apt-daily and apt-daily-upgrade services [ ], failed e2scrub_all.service & user@ systemd units [ ][ ] as well as generic build failures [ ].arm64 architecture nodes hosted at/by codethink.co.uk. [ ]rb-general@lists.reproducible-builds.org
#reproducible-builds on irc.oftc.net.



:wq for today.
 I've been using Vim as my main text editor for 18 years, but for most of that
time I've been using something very close to the default configuration: my
I've been using Vim as my main text editor for 18 years, but for most of that
time I've been using something very close to the default configuration: my
vimrc contained not much more than preferences for indentation and how to
visually indicate white space characters like tabs.
Last but not least, I've used a single colour scheme for most of that time:
Zenburn.
In 20151 I started exploring a few Vim plugins2. To manage
them, I started by choosing a plugin manager,
Pathogen3. Recently I
noticed that the plugin's author, Tim Pope, now recommends new users just use
Vim's built in package management instead. I got curious about Tim Pope's
other plugins: He has written a great deal of them.
Given I've spent most of two decades with a barely-configured Vim, you can
imagine that I don't want to radically alter the way it works, and so I did
not expect to want to use a lot of plugins. The utility of a plugin would have
to outweight the disadvantages of coming to rely on one. But when browsing
Tim's plugins, time and time again, I found myself reacting to description
with How did I manage without this?. And so, I've ended up installing all
of the following, all by Tim Pope:
gaYYYY-MM-DD) properly with the increment/decrement functions (<C-A>, <C-X>):cnext and :cprevious I ve spent a bit of time playing with
vxlan - which is very neat, but also incredibly insecure by default.When using vxlan, be very careful to understand how the host is connected to the internet. The kernel will listen on all interfaces for packets, which means hosts accessable to VMs it s hosting (e.g., by bridged interface or a private LAN will accept packets from VMs and inject them into arbitrary VLANs, even ones it s not on.I reported this to the kernel mailing list to no reply with more technical details.The tl;dr is:
I ve spent a bit of time playing with
vxlan - which is very neat, but also incredibly insecure by default.When using vxlan, be very careful to understand how the host is connected to the internet. The kernel will listen on all interfaces for packets, which means hosts accessable to VMs it s hosting (e.g., by bridged interface or a private LAN will accept packets from VMs and inject them into arbitrary VLANs, even ones it s not on.I reported this to the kernel mailing list to no reply with more technical details.The tl;dr is: $ ip link add vevx0a type veth peer name vevx0z
$ ip addr add 169.254.0.2/31 dev vevx0a
$ ip addr add 169.254.0.3/31 dev vevx0z
$ ip link add vxlan0 type vxlan id 42 \
local 169.254.0.2 dev vevx0a dstport 4789
$ # Note the above 'dev' and 'local' ip are set here
$ ip addr add 10.10.10.1/24 dev vxlan0
results in vxlan0 listening on all interfaces, not just vevx0z or vevx0a. To prove it to myself, I spun up a docker container (using a completely different network bridge with no connection to any of the interfaces above), and ran a Go program to send VXLAN UDP packets to my bridge host:
$ docker run -it --rm -v $(pwd):/mnt debian:unstable /mnt/spam 172.17.0.1:4789 $which results in packets getting injected into my vxlan interface
$ sudo tcpdump -e -i vxlan0 tcpdump: verbose output suppressed, use -v[v]... for full protocol decode listening on vxlan0, link-type EN10MB (Ethernet), snapshot length 262144 bytes 21:30:15.746754 de:ad:be:ef:00:01 (oui Unknown) > Broadcast, ethertype IPv4 (0x0800), length 64: truncated-ip - 27706 bytes missing! 33.0.0.0 > localhost: ip-proto-114 21:30:15.746773 de:ad:be:ef:00:01 (oui Unknown) > Broadcast, ethertype IPv4 (0x0800), length 64: truncated-ip - 27706 bytes missing! 33.0.0.0 > localhost: ip-proto-114 21:30:15.746787 de:ad:be:ef:00:01 (oui Unknown) > Broadcast, ethertype IPv4 (0x0800), length 64: truncated-ip - 27706 bytes missing! 33.0.0.0 > localhost: ip-proto-114 21:30:15.746801 de:ad:be:ef:00:01 (oui Unknown) > Broadcast, ethertype IPv4 (0x0800), length 64: truncated-ip - 27706 bytes missing! 33.0.0.0 > localhost: ip-proto-114 21:30:15.746815 de:ad:be:ef:00:01 (oui Unknown) > Broadcast, ethertype IPv4 (0x0800), length 64: truncated-ip - 27706 bytes missing! 33.0.0.0 > localhost: ip-proto-114 21:30:15.746827 de:ad:be:ef:00:01 (oui Unknown) > Broadcast, ethertype IPv4 (0x0800), length 64: truncated-ip - 27706 bytes missing! 33.0.0.0 > localhost: ip-proto-114 21:30:15.746870 de:ad:be:ef:00:01 (oui Unknown) > Broadcast, ethertype IPv4 (0x0800), length 64: truncated-ip - 27706 bytes missing! 33.0.0.0 > localhost: ip-proto-114 21:30:15.746885 de:ad:be:ef:00:01 (oui Unknown) > Broadcast, ethertype IPv4 (0x0800), length 64: truncated-ip - 27706 bytes missing! 33.0.0.0 > localhost: ip-proto-114 21:30:15.746899 de:ad:be:ef:00:01 (oui Unknown) > Broadcast, ethertype IPv4 (0x0800), length 64: truncated-ip - 27706 bytes missing! 33.0.0.0 > localhost: ip-proto-114 21:30:15.746913 de:ad:be:ef:00:01 (oui Unknown) > Broadcast, ethertype IPv4 (0x0800), length 64: truncated-ip - 27706 bytes missing! 33.0.0.0 > localhost: ip-proto-114 10 packets captured 10 packets received by filter 0 packets dropped by kernel(the program in question is the following:)
package main
import (
"net"
"os"
"github.com/mdlayher/ethernet"
"github.com/mdlayher/vxlan"
)
func main()
conn, err := net.Dial("udp", os.Args[1])
if err != nil panic(err)
for i := 0; i < 10; i++
vxf := &vxlan.Frame
VNI: vxlan.VNI(42),
Ethernet: ðernet.Frame
Source: net.HardwareAddr 0xDE, 0xAD, 0xBE,
0xEF, 0x00, 0x01 ,
Destination: net.HardwareAddr 0xFF, 0xFF, 0xFF,
0xFF, 0xFF, 0xFF ,
EtherType: ethernet.EtherTypeIPv4,
Payload: []byte("Hello, World!"),
,
frb, err := vxf.MarshalBinary()
if err != nil panic(err)
_, err = conn.Write(frb)
if err != nil panic(err)
When using vxlan, be absolutely sure all hosts that can address any interface on the host are authorized to send arbitrary packets into any VLAN that box can send to, or there s very careful and specific controls and firewalling. Note this includes public interfaces (e.g., dual-homed private network / internet boxes), or any type of dual-homing (VPNs, etc).
https://lists.debian.org/debian-vote/2021/11/msg00034.htmlPrevious drafts and resulting discussion are at:
https://lists.debian.org/debian-vote/2021/10/msg00002.htmland also see the discussion thread starting here:
https://lists.debian.org/debian-vote/2021/09/msg00010.html
https://lists.debian.org/debian-vote/2021/10/msg00019.html
Server refused public-key signature despite accepting key!
Sep 20 13:10:32 container001 sshd[1647842]: Accepted key RSA SHA256:t3DVS5wZmO7DVwqFc41AvwgS5gx1jDWnR89apGmFpf4 found at /home/XXXXXXXXX/.ssh/authorized_keys:6
Sep 20 13:10:32 container001 sshd[1647842]: debug1: restore_uid: 0/0
Sep 20 13:10:32 container001 sshd[1647842]: Postponed publickey for XXXXXXXXX from xxx.xxx.xxx.xxx port 63579 ssh2 [preauth]
Sep 20 13:10:33 container001 sshd[1647842]: debug1: userauth-request for user XXXXXXXXX service ssh-connection method publickey [preauth]
Sep 20 13:10:33 container001 sshd[1647842]: debug1: attempt 2 failures 0 [preauth]
Sep 20 13:10:33 container001 sshd[1647842]: debug1: temporarily_use_uid: 1000/1000 (e=0/0)
Sep 20 13:10:33 container001 sshd[1647842]: debug1: trying public key file /home/XXXXXXXXX/.ssh/authorized_keys
Sep 20 13:10:33 container001 sshd[1647842]: debug1: fd 5 clearing O_NONBLOCK
Sep 20 13:10:33 container001 sshd[1647842]: debug1: /home/XXXXXXXXX/.ssh/authorized_keys:6: matching key found: RSA SHA256:t3DVS5wZmO7DVwqFc41AvwgS5gx1jDWnR89apGmFpf4
Sep 20 13:10:33 container001 sshd[1647842]: debug1: /home/XXXXXXXXX/.ssh/authorized_keys:6: key options: agent-forwarding port-forwarding pty user-rc x11-forwarding
Sep 20 13:10:33 container001 sshd[1647842]: Accepted key RSA SHA256:t3DVS5wZmO7DVwqFc41AvwgS5gx1jDWnR89apGmFpf4 found at /home/XXXXXXXXX/.ssh/authorized_keys:6
Sep 20 13:10:33 container001 sshd[1647842]: debug1: restore_uid: 0/0
Sep 20 13:10:33 container001 sshd[1647842]: debug1: auth_activate_options: setting new authentication options
Sep 20 13:10:33 container001 sshd[1647842]: Failed publickey for XXXXXXXXX from xxx.xxx.xxx.xxx port 63579 ssh2: RSA SHA256:t3DVS5wZmO7DVwqFc41AvwgS5gx1jDWnR89apGmFpf4
Sep 20 13:10:39 container001 sshd[1647514]: debug1: Forked child 1648153.
Sep 20 13:10:39 container001 sshd[1648153]: debug1: Set /proc/self/oom_score_adj to 0
Sep 20 13:10:39 container001 sshd[1648153]: debug1: rexec start in 5 out 5 newsock 5 pipe 8 sock 9
Sep 20 13:10:39 container001 sshd[1648153]: debug1: inetd sockets after dupping: 4, 4
ferm
first", "you need an extra reboot here", or "this is how you finish
the PostgreSQL upgrade".
With Debian getting closer to a 2 year release cycle, with the
previous release being supported basically only one year after the
new stable comes out, I feel more and more strongly that this needs
better automation.
So I'm thinking that I should write a prototype for this. Ubuntu has
do-release-upgrade that is too Ubuntu-specific to be reused. An
attempt at collaborating on this has been mostly met with silence
from Ubuntu's side as well.
I'm thinking that using something like Fabric, Mitogen, or
Transilience: anything that will allow me to write simple,
portable Python code that can run transparently on a local machine
(for single systems upgrades, possibly with a GUI frontend) to remote
servers (for large clusters of servers, maybe with canaries and
grouping using Cumin). I'll note that Koumbit started
experimenting with Puppet Bolt in the bullseye upgrade process,
but that feels too site-specific to be useful more broadly.
Thanks to lelutin and pabs for reviewing a draft of this post.
 I have been Debian Stretch running on my HP Pavilion 14-ce0000nq laptop since buying it back in April 2019, just before my presence at Oxidizeconf where I presented "How to Rust When Standards Are Defined in C".Debian Buster (aka Debian 10) was released about 4 months later and I've been postponing the upgrade as my free time isn't what it used to be. I also tend to wait for the first or even second update of the release to avoid any sharp edges.As this laptop has a Realtek 8821CE wireless card that wasn't officially supported in the Linux kernel, I had to use an out-of-tree hacked driver to have the wireless work on Stretch kernels such as 4.19, it didn't even got along with DKMS, so all compilations and installations of it, I did them manually. More reason to wait for a newer release that would contain a driver inside the official kernel.I was waiting for the inevitable and dreading the wireless issues, but since mid-august Bullseye became stable, turning Stretch into oldoldstable, I decided that I had to do the upgrade, at least to buster.The Grub error and the fix
I have been Debian Stretch running on my HP Pavilion 14-ce0000nq laptop since buying it back in April 2019, just before my presence at Oxidizeconf where I presented "How to Rust When Standards Are Defined in C".Debian Buster (aka Debian 10) was released about 4 months later and I've been postponing the upgrade as my free time isn't what it used to be. I also tend to wait for the first or even second update of the release to avoid any sharp edges.As this laptop has a Realtek 8821CE wireless card that wasn't officially supported in the Linux kernel, I had to use an out-of-tree hacked driver to have the wireless work on Stretch kernels such as 4.19, it didn't even got along with DKMS, so all compilations and installations of it, I did them manually. More reason to wait for a newer release that would contain a driver inside the official kernel.I was waiting for the inevitable and dreading the wireless issues, but since mid-august Bullseye became stable, turning Stretch into oldoldstable, I decided that I had to do the upgrade, at least to buster.The Grub error and the fix error: symbol grub_is_lockdown not foundI looked for a solution and it seemed everyone was stuck or the solution was unclear.There is even a bug report in Debian about this error, bug #984760.
update-grub22) reinstall grub-efi-amd64 and make Debian the default
dpkg-reconfigure -plow grub-efi-amd64When reinstalling grub-efi-amd64 onto the disk, I think the scariest questions were to these:
andForce extra installation to the EFI removable media path?
Some EFI-based systems are buggy and do not handle new bootloaders correctly. If you force an extra installation of GRUB to the EFI removable media path, this should ensure that this system will boot Debian correctly despite such a problem. However, it may remove the ability to boot any other operating systems that also depend on this path. If so, you will need to make sure that GRUB is configured successfully to be able to boot any other OS installations correctly.
Update NVRAM variables to automatically boot into Debian?I think the first can be safely answered "No" if you don't plan on booting via a removable USB stick, while the second is the one that does the restoring.The second question is probably safe if you don't use PXE boot or other boot method, at least that's what I understand. But if you do, I suspect by installing refind, by playing with the multiple efi* named packages and tools, you can restore that, or it might be that your BIOS allows that directly.
GRUB can configure your platform's NVRAM variables so that it boots into Debian automatically when powered on. However, you may prefer to disable this behavior and avoid changes to your boot configuration. For example, if your NVRAM variables have been set up such that your system contacts a PXE server on every boot, this would preserve that behavior.
eddy@aptonia:/ $ cat /etc/modulesThe 5.10 compatible driver for RTL8821CE wireless adapterAfter the upgrade to Buster, the oldstable version of the kernel, 4.19, the hacked version of the driver I've been using on Stretch on 4.9 kernels was no longer compatible - failed to compile due to missing symbols.The fix for me was to switch to the DKMS compatible driver from https://github.com/tomaspinho/rtl8821ce, as this seems to work for both 4.19 and 5.10 kernels (installed from backports).
# /etc/modules: kernel modules to load at boot time.
#
# This file contains the names of kernel modules that should be loaded
# at boot time, one per line. Lines beginning with "#" are ignored.
r8169
DRV_NAME=rtl8821ceBut you just build and install them only for the select kernel versions of your choice:
DRV_VERSION=v5.5.2_34066.20200325
cp -r . /usr/src/$ DRV_NAME -$ DRV_VERSION
dkms add -m $ DRV_NAME -v $ DRV_VERSION
dkms build -m $ DRV_NAME -v $ DRV_VERSION -k 5.10.0-0.bpo.8-amd64Or, without the variables:
dkms install -m $ DRV_NAME -v $ DRV_VERSION -k 5.10.0-0.bpo.8-amd64
dkms build rtl8821ce/v5.5.2_34066.20200325 -k 4.19.0-17-amd64dkms status should confirm everything is in place and I think you need to update grub2 again after this.
dkms install rtl8821ce/v5.5.2_34066.20200325 -k 4.19.0-17-amd64



:wq for today.
 After nearly two years, the RApiDatetime package on CRAN has received an update, followed-up a quick bug fix.
RApiDatetime provides a number of entry points for C-level functions of the R API for
After nearly two years, the RApiDatetime package on CRAN has received an update, followed-up a quick bug fix.
RApiDatetime provides a number of entry points for C-level functions of the R API for Date and Datetime calculations. The functions asPOSIXlt and asPOSIXct convert between long and compact datetime representation, formatPOSIXlt and Rstrptime convert to and from character strings, and POSIXlt2D and D2POSIXlt convert between Date and POSIXlt datetime. Lastly, asDatePOSIXct converts to a date type. All these functions are rather useful, but were not previously exported by R for C-level use by other packages. Which this package aims to change.
This pair of releases updates the code to the current R-devel standard, and refreshes a few standard packaging aspects starting from making builds on the Windows UCRT platform possible. And while making an accomodation for one beloved architecture (in release 0.0.5), we introduced another issue on another almost equally beloved platform which 0.0.6 clears up. It should be ready and stable now.
Courtesy of my CRANberries, there is are comparisons to the previous release 0.0.5, and 0.0.4, respectively. More information is on the rapidatetime page. For questions or comments please use the issue tracker off the GitHub repo.Changes in RApiDatetime version 0.0.6 (2021-08-13)
- Correctly account for SunOS to have it avoid
GMTOFFuse- A new test file was added to ensure NEWS.Rd is always at the current release version.
Changes in RApiDatetime version 0.0.5 (2021-08-05)
- Add a few
#nocovtags- Update continuous integration to use r-ci, reenable coverage
- Update DESCRIPTION with URL and BugReports fields
- Add new CI and LastCommitted badges to README.md
- Add compiler flag for Windows UCRT build
- Synchronized datetime function with upstream r-devel code
This post by Dirk Eddelbuettel originated on his Thinking inside the box blog. Please report excessive re-aggregation in third-party for-profit settings.
 If I have seen further, it is by standing on the shoulders of Giants Issac Newton, 1675. Although it should be credited to 12th century Bernard of Chartres. You will know why I have shared this, probably at the beginning of Civil Aviation history itself.
If I have seen further, it is by standing on the shoulders of Giants Issac Newton, 1675. Although it should be credited to 12th century Bernard of Chartres. You will know why I have shared this, probably at the beginning of Civil Aviation history itself.
 But yes, it needs it own space, maybe after some more time.
Report on Standing Committee on IP Regulation in India and the false promises.
Again, I do not want to take much time in sharing details about what the report contains, as the report can be found here. I have uploaded it on WordPress, in case of an issue. An observation on the same subject can be found here. At least, to me and probably those who have been following the IP space as either using/working on free software or even IP would be aware that the issues shared have been known since 1994. And it does benefit the industry rather than the country. This way, the rent-seekers, and monopolists win. There is ample literature that shared how rich countries had weak regulation for decades and even centuries till it was advantageous for them to have strong IP. One can look at the history of Europe and the United States for it. We can also look at the history of our neighbor China, which for the last 5 decades has used some provision of IP and disregarded many others. But these words are of no use, as the policies done and shared are by the rich for the rich.
But yes, it needs it own space, maybe after some more time.
Report on Standing Committee on IP Regulation in India and the false promises.
Again, I do not want to take much time in sharing details about what the report contains, as the report can be found here. I have uploaded it on WordPress, in case of an issue. An observation on the same subject can be found here. At least, to me and probably those who have been following the IP space as either using/working on free software or even IP would be aware that the issues shared have been known since 1994. And it does benefit the industry rather than the country. This way, the rent-seekers, and monopolists win. There is ample literature that shared how rich countries had weak regulation for decades and even centuries till it was advantageous for them to have strong IP. One can look at the history of Europe and the United States for it. We can also look at the history of our neighbor China, which for the last 5 decades has used some provision of IP and disregarded many others. But these words are of no use, as the policies done and shared are by the rich for the rich.
 kisi ke baap ka hindustan todi hain Rahat Indori
kisi ke baap ka hindustan todi hain Rahat Indori  Continuing with #newinbullseye. One package that isn t new but its tools are used by many of us is util-linux, providing many essential system utilities. There is util-linux v2.33.1 in Debian/buster and util-linux v2.36.1 in Debian/bullseye, and as usual there are many new features and options available.
I don t want to replicate the release notes provided by upstream, instead make sure to check out the
Continuing with #newinbullseye. One package that isn t new but its tools are used by many of us is util-linux, providing many essential system utilities. There is util-linux v2.33.1 in Debian/buster and util-linux v2.36.1 in Debian/bullseye, and as usual there are many new features and options available.
I don t want to replicate the release notes provided by upstream, instead make sure to check out the Release highlights sections in the following release notes:
Tools that have been taken over from / moved to other packages
Debian s util-linux source package provides new binary packages: eject (and eject-udeb) and bsdextrautils. The util-linux implementation of /usr/bin/eject is used now, replacing the one previously provided by the eject source package.
Overall, from a util-linux perspective the following shifts took place:
col, colcrt, colrm, column: moved from binary package bsdmainutils to bsdextrautilseject: moved to binary package ejecthd: moved from binary package bsdmainutils to bsdextrautilshexdump: moved from binary package bsdmainutils to bsdextrautilslook: moved from binary package bsdmainutils to bsdextrautilsul: moved from binary package bsdmainutils to bsdextrautilswrite(.ul): moved from binary package bsdmainutils (named bsd-write) to bsdextrautils/usr/bin/rename.ul (rename files): use e.g. rename package instead, see #926637 for details regarding the removal/usr/bin/volname (return volume name for a device formatted with an ISO-9660 file system): use blkid -s LABEL -o value $filename instead/usr/lib/eject/dmcrypt-get-device: no replacement available
scriptlive: re-execute stdin log by a shell in PTY sessionlsirq + irqtop (to monitor kernel interrupts) sadly didn t make it into util-linux s packaging of Debian/bullseye (as without per-CPU data they do not seem mature at this time). The new hardlink tool (to consolidate duplicate files via hardlinks) won t be shipped, as there s an existing hardlink package already.
New features/options
agetty + getty:
--show-issue display issue file and exitblkdiscard:
--force disable all checkingblkid:
-D, --no-part-details don't print info from partition tableblkzone:
Commands: open Open a range of zones. close Close a range of zones. finish Set a range of zones to Full. Options: -f, --force enforce on block devices used by the systemcfdisk:
--lock[=<mode>] use exclusive device lock (yes, no or nonblock)dmesg:
--noescape don't escape unprintable character -W, --follow-new wait and print only new messagesfdisk:
-x, --list-details like --list but with more details -n, --noauto-pt don't create default partition table on empty devices --lock[=<mode>] use exclusive device lock (yes, no or nonblock)fstrim:
-I, --listed-in <list> trim filesystems listed in specified files --quiet-unsupported suppress error messages if trim unsupportedlsblk:
Options:
-E, --dedup <column> de-duplicate output by <column>
(for example 'lsblk --dedup WWN' to de-duplicate devices by WWN number, e.g. multi-path devices)
-M, --merge group parents of sub-trees (usable for RAIDs, Multi-path)
see http://karelzak.blogspot.com/2018/11/lsblk-merge.html
New output columns:
FSVER filesystem version
PARTTYPENAME partition type name
DAX dax-capable device
lscpu:
Options:
-B, --bytes print sizes in bytes rather than in human readable format
-C, --caches[=<list>] info about caches in extended readable format
--output-all print all available columns for -e, -p or -C
Available output columns for -C:
ALL-SIZE size of all system caches
LEVEL cache level
NAME cache name
ONE-SIZE size of one cache
TYPE cache type
WAYS ways of associativity
ALLOC-POLICY allocation policy
WRITE-POLICY write policy
PHY-LINE number of physical cache line per cache t
SETS number of sets in the cache; set lines has the same cache index
COHERENCY-SIZE minimum amount of data in bytes transferred from memory to cache
lslogins:
--lastlog <path> set an alternate path for lastloglsns:
-t, --type time namespace type time is also supported now (next to mnt, net, ipc, user, pid, uts, cgroup)mkswap:
--lock[=<mode>] use exclusive device lock (yes, no or nonblock)more:
Options: -n, --lines <number> the number of lines per screenful New long options (in addition to the listed equivalent short options): --silent - equivalent to -d --logical - equivalent to -f --no-pause - equivalent to -l --print-over - equivalent to -c --clean-print - equivalent to -p --squeeze - equivalent to -s --plain - equivalent to -umount:
Options: --target-prefix <path> specifies path use for all mountpoints Source: ID=<id> specifies device by udev hardware IDmountpoint:
--nofollow do not follow symlinknsenter:
-T, --time[=<file>] enter time namespacescript:
-I, --log-in <file> log stdin to file -O, --log-out <file> log stdout to file (default) -B, --log-io <file> log stdin and stdout to file -T, --log-timing <file> log timing information to file -m, --logging-format <name> force to 'classic' or 'advanced' format -E, --echo <when> echo input (auto, always or never)sfdisk:
--disk-id <dev> [<str>] print or change disk label ID (UUID) --relocate <oper> <dev> move partition header --move-use-fsync use fsync after each write when move data --lock[=<mode>] use exclusive device lock (yes, no or nonblock)unshare:
-T, --time[=<file>] unshare time namespace --map-user=<uid> <name> map current user to uid (implies --user) --map-group=<gid> <name> map current group to gid (implies --user) -c, --map-current-user map current user to itself (implies --user) --keep-caps retain capabilities granted in user namespaces -R, --root=<dir> run the command with root directory set to <dir> -w, --wd=<dir> change working directory to <dir> -S, --setuid <uid> set uid in entered namespace -G, --setgid <gid> set gid in entered namespace --monotonic <offset> set clock monotonic offset (seconds) in time namespaces --boottime <offset> set clock boottime offset (seconds) in time namespaceswipefs:
--lock[=<mode>] use exclusive device lock (yes, no or nonblock)
| Series: | Deep Witches #0 |
| Publisher: | A Girl and Her Fed Books |
| Copyright: | September 2017 |
| ASIN: | B075PHK498 |
| Format: | Kindle |
| Pages: | 226 |
Next.